DNSSEC signing service
PCH operates the world’s largest DNSSEC public signing service, and the only one which meets or exceeds the security of the DNS root itself.
DNSSEC is crucial in securing the authenticity of DNS data and it is the underlying foundation for DANE, the technology that is replacing Certificate Authorities in securing web traffic. But no security chain is stronger than its weakest link. By using PCH's DNSSEC signing service, domain administrators maintain the highest possible level of security at each step of the domain resolution process, something that’s not possible using any other platform.

As the only operator of a FIPS 140-2 Level 4 DNSSEC and Common Criteria EAL4+ signing platform other than ICANN itself (who sign the root zone), since 2011, PCH has offered the highest level of DNSSEC confidence available.
The PCH DNSSEC signing service meets or exceeds the security of ICANN's DNSSEC signing process in all respects, with the additional benefit of being geopolitically distributed, rather than constrained within the single jurisdiction of the United States, as the root is. PCH's key management occurs in physical security facilities which we own and operate in Zürich, Switzerland; San Jose, California; and Singapore. In addition to security, PCH’s service features high availability: 100% uptime since it entered production in April, 2011, and that high availability is a consequence of our highly redundant facilities and operational practices.
A cornerstone of our organizational philosophy is that transparency is the only route to high security, and this works hand-in-hand with our not-for-profit mission to enhance Internet infrastructural security through knowledge transfer and the open dissemination of best practices and technological improvement. By creating a best-practice implementation that is simultaneously completely open-sourced, we ensure that domain administrators who use our signing platform are able not only to audit it fully, but also to appropriate and copy each and every part of it, and migrate to a self-operated solution as they desire to and become comfortable with the technology.
For more information contact our DNS services group.
Links:Physical Security
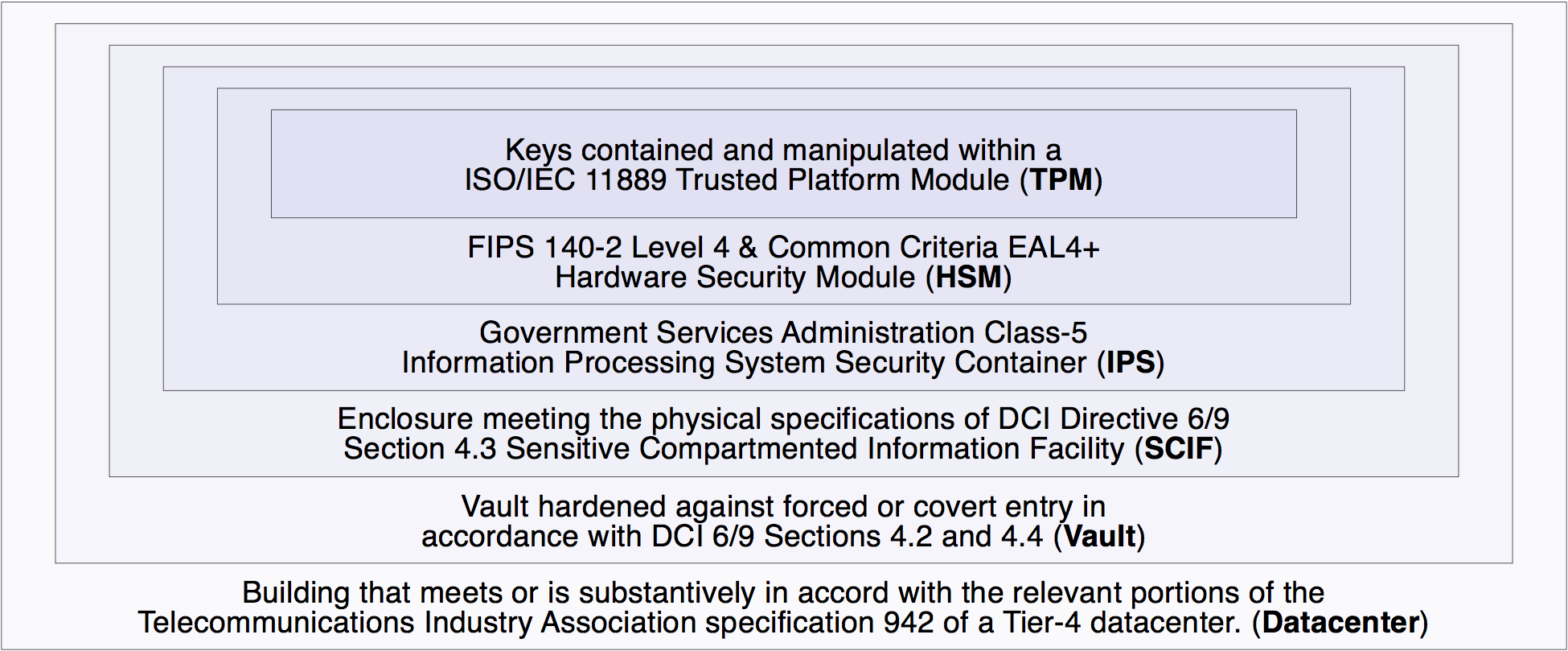
In each facility, cryptographic key material is utilized solely within an ISO/IEC 11889 Trusted Platform Module (TPM). The TPM is an integral component of a FIPS 140-2 Level 4 and Common Criteria EAL4+ Hardware Security Module (HSM). In the Zurich, San Jose and Singapore facilities, which are in finished form, the HSM, in turn, is protected within a GSA Class-5 IPS Security Container (IPS). The IPS, in turn, is contained within an enclosure meeting the physical specifications of a DCI Directive 6/9 Section 4.3 Sensitive Compartmented Information Facility (SCIF). The SCIF, in turn, is enclosed within a vault that has been hardened against forced or covert entry in accordance with DCI 6/9 Sections 4.2 and 4.4, and the interior of which is under constant video recording and other monitoring. This vault, in turn, is housed within a building that meets or is substantively in accord with the relevant portions of the Telecommunications Industry Association specification 942 of a Tier-4 datacenter. In addition, the Zurich facility meets the requirements of FEMA TR-87 Standards for Fallout Shelters and the Swiss Federal Office for Civil Protection TWK 1994 - Technische Weisung für die Konstruktion und Bemessung von Schutzbauten (“Technical Directive for the construction and design of nuclear protection structures”) and its subsidiary documents. In the current Berkeley KSK facility, the HSM is stored in an unloaded state (containing no cryptographic key material) in a business-grade safe, while a permanent Berkeley IPS, SCIF, and vault are under construction.
Together, the TPM, HSM, IPS, SCIF, Vault, and Datacenter comprise six concentric layers of physical security, each successively harder to compromise than the last, to provide tamper resistance and tamper evidence protecting the key material and zone-signing process at each location.